Some are sold per user, per org, per app, per line of code analyzed. See these examples and this report for details. Some tools are starting to move into the IDE. FindBugs is a highly configurable tool, that allows loading custom rule sets. Graudit - Scans multiple languages for various security flaws. Puma Scan Professional - A. Flawfinder checks for calls to known potentially vulnerable library function calls.
| Uploader: | Malalar |
| Date Added: | 15 May 2014 |
| File Size: | 16.69 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 13380 |
| Price: | Free* [*Free Regsitration Required] |
For a basic run, you can enter the following command; Visualcodegrepper. Developed by Nick Dunn, and currently on version 2. Run application in console only hide GUI. The tool comes with over default searches that identify SQL injection, cross-site scripting XSSinsecure remote and local file includes, hard-coded passwords, and much more.
Use this option either to load target immediately into GUI or to provide the target for console mode. PT AI helps to easily understand, verify, and fix flaws; has a simple UI; is highly automated and easy to use.
Pychecker Free stand-alone script This static analyzer focuses on finding bugs.
More info Appendix A: Automatically export results to a file in the specified format. Checks for conformity to Lionel Cons' Perl guide.
Source Code Analysis Tools
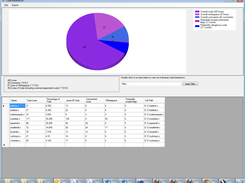
Below is an example command. After analyzing the code VCG outputs a pie chart of results, which represents the number of lines grepprr code which were scanned, the overall whitespace, the overall comments, potentially broken or unfinished flags and potentially dangerous code. Once you have finished downloading the setup, run the installer to start the installation. Analysts frequently can't compile code because they don't have the right libraries, all the compilation instructions, all the code, etc.
Strengths and Weaknesses Strengths Scales well -- can be run on lots of software, and can be run repeatedly as with nightly builds or continuous integration Useful for things that such tools can automatically find with high confidence, such as buffer overflows, SQL Injection Flaws, and so forth Output is good for developers -- highlights the precise source files, line numbers, and even subsections of lines that are affected Weaknesses Many types of security vulnerabilities are difficult to find automatically, such as authentication problems, access control issues, insecure use of cryptography, etc.
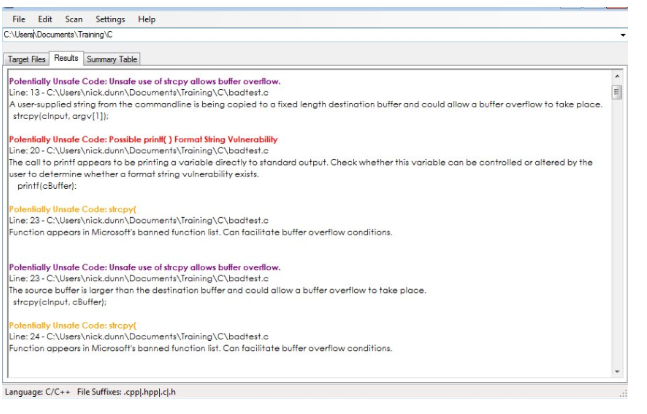
One great feature of VCG is viual it lets you know the line number of the code with the vulnerability and the type of vulnerability it possesses. For example, if you want to exclude the comments from being analyzed, you can choose the Scan Code Only option.
Static Code Analysis SCA is the analysis done on computer software without actually executing the code.
Many of these tools have difficulty analyzing code that can't be compiled. Once we run this command, the program searches for the target file given, and if it contains any files that contain Java code, it analyzes the code, and saves the result in a text file.
Not only does this tool perform complex checks, it also has a configuration file for each language that allows the user to run custom queries. Can it run against binaries instead of source? Critic Free perl module The default configuration of Perl:: None of the vulnerabilities it finds cannot be modified right there on the application itself -- users are prompted to use a separate tool for that.
See these examples and this report for details.
Source Code Analysis Tools - OWASP
Set target file or directory. The tools listed in the tables below are presented in alphabetical order.
vissual Suspicious comment indicating broken code - Dark Blue. If you have multiple class files inside the directory you selected, everything will be loaded into the application and each one will be analyzed.

Integrates with tools such as Brakeman, Bandit, FindBugs, and others. For the viwual of problems that can be detected during the software development phase itself, this is a powerful phase within the development life cycle to employ such tools, as it provides immediate feedback to the developer on issues they might be introducing into the code during code development itself. Although it might look like outdated its home page is announcing visuao for PHP4Pixy is doing an outstanding job when looking for Cross-Site Scripting vulnerabilities and SQL or code injections.
Some tools are starting to move into the IDE. The current greepper of the art only allows such tools to automatically find a relatively small percentage of application security flaws. Line number - File name. Running VCG using the command prompt.

No comments:
Post a Comment